Using ansible to Setup Port Forwarding
Introduction
In its simplest form, ansible is a Python derived automation scripting tool, commonly used to install, configure and manage servers and services. It has a huge collection of modules available out of the box to support management of a wide variety of tasks.
In this blog, we’re going to talk about using ansible to setup TCP/IP port forwarding to support a zDT – which is a zSeries mainframe emulator – that runs as a guest inside a Linux server.
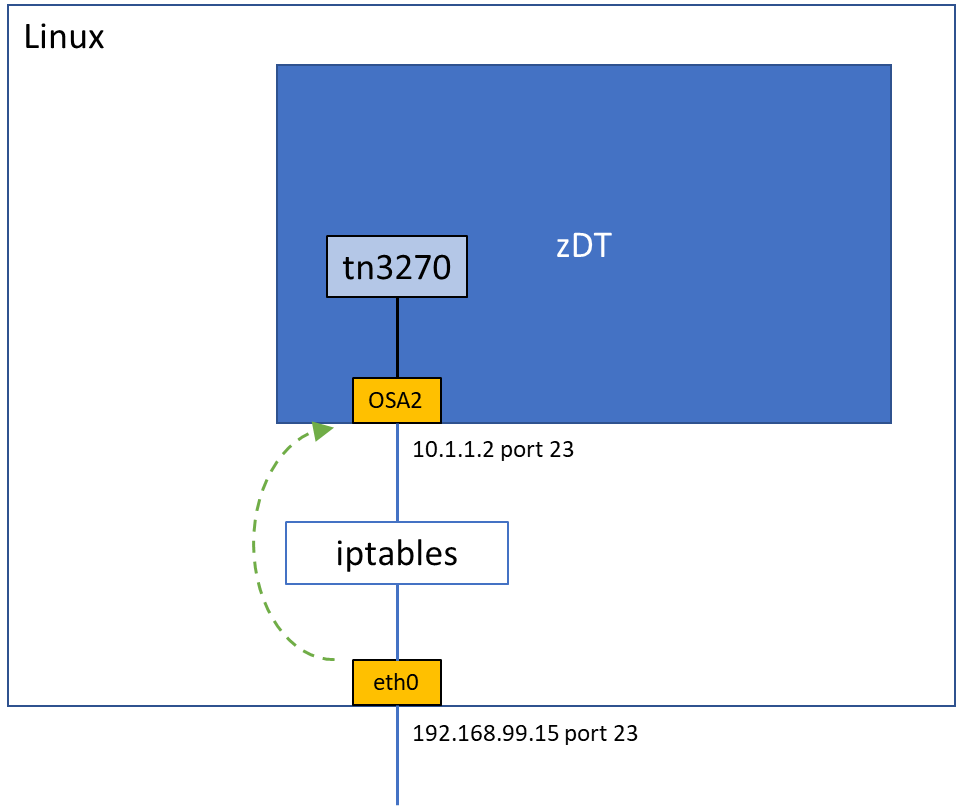
In this example, the zDT emulated mainframe is presented inside the Linux server (at one end of a tun/tap tunnel) on IP address 10.1.1.2, and the host Linux server appears on the physical network as 192.168.99.15. For client applications and tools to be able to connect to the zDT services, the Linux server will need to forward those requests from 192.168.99.15 to the internal 10.1.1.2. This can be done by either:
- Making the client machine aware that it needs to route requests for 10.1.1.2 via 192.168.99.15 – which would require a “route add” on every potential client machine, or
- Forward the important ports using iptables (as in the diagram) and letting the clients connect to the Linux host.
The port forwarding works like this:
- Client terminal emulation program requests a connection and session to the Linux host, port 23
- Linux iptables forward this request on to port 23 on the zDT IP address (10.1.1.2)
This is possible because we use a feature of the firewall (NAT) to hide the fact that we’ve done this from the client.
Suffice to say, whilst the example is a little esoteric, the tools and method are quite normal. In our case we’re forwarding to a service hosted within the same Linux, but this can be applied just as well to an external address.
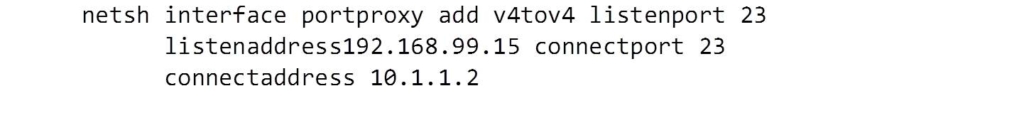
Setting up port forwarding is also possible on Windows, where the netsh command is used (see below).
General Form of (Linux) iptables Port Forwarding Commands
The iptables commands to do this all revolve around the NAT (network address translation) table, and all have to be issued with root authority (cf sudo).
General Form of (Windows) netsh Port Forwarding Commands
To create a new port forwarding rule:
Script to Apply Port Forwarding
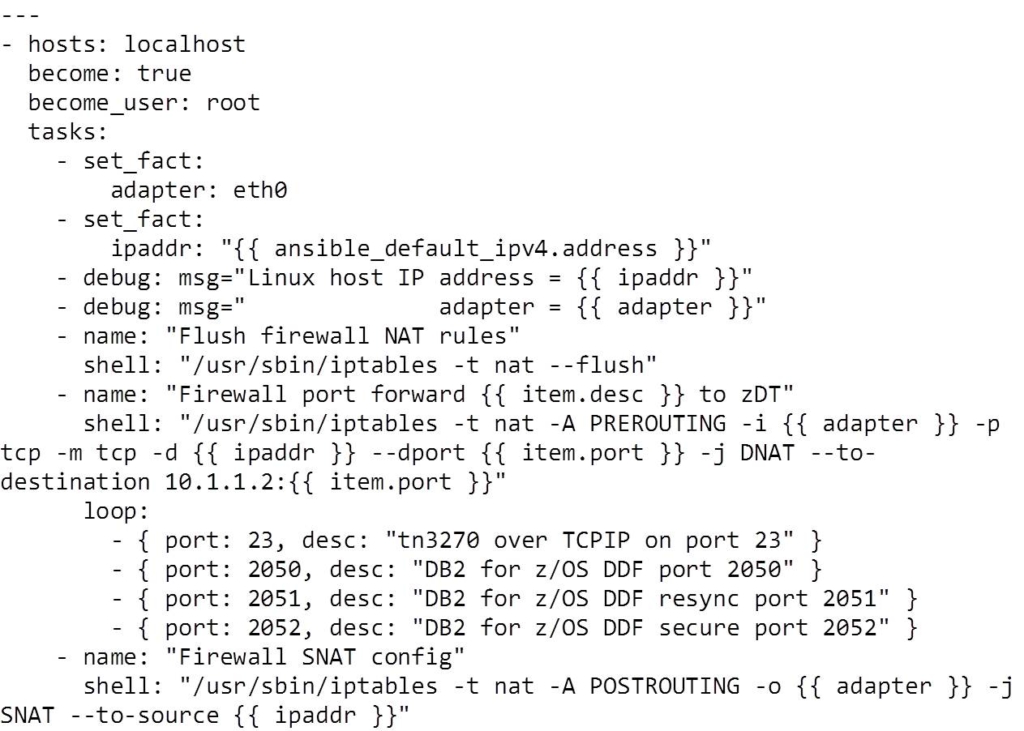
Here’s our ansible script:
Things to note:
- We’re running on the local machine as root (required for iptables)
- Set a couple of variables to name the adapter and the default IP address and then report the values used with the debug module
- Use a shell command to clear the NAT rules
- Loop a shell command (to establish the port forwarding PREROUTING DNAT rule) for four different ports
- Use a shell command to set the POSTROUTING SNAT rule
Ansible has a module to apply iptables firewall changes, but the parameters and names do not directly map to the iptables command, making the syntax confusing to read. As seen above, I’ve stuck with the iptables command, but someone with more experience might make use of the iptables module to achieve the same thing.
This is what the output looks like:

Leave a Reply